Years ago, hacking into another person’s device to get a peep at their call logs or text messages seemed to be a farfetched idea. But in the digital age that we live in, anyone can do it using the right tool.
Cloning a target device can today be done even by the people who don’t possess any technical know-how. This has been made possible due to advanced applications which can grant you anonymous access to all data on the target device, and that too, within minutes.
Just configure such a device as per the given instructions and you’re good to go.
Would you like to discover one such tool? Well, join us as we introduce the best cell cloning app out there.
Why Clone a Cell Phone?
There are several triggers that could prompt you to clone someone’s phone:
- To figure out if your child is being bullied – A look at his/her text messages and social activity can let you in on this.
- To catch your spouse cheating – Tracking his/her calls and live GPS location can give you clues about who they’re in touch with and where they go.
- To find out if your employees are loyal – Going through their calls and texts can tell you what they’re up to.
Regardless of what exactly pushes you to do it, getting inside someone else’s phone can indeed come handy. And while doing so, one of the primary things you need to do is ensure that your target person never finds out that you’re spying on them.
Our favorite app among the hundreds of phone cloning solutions out there is Spyier. It comes equipped with a ton of nifty features which help you achieve your purpose without hassle and also protects your identity while doing it. Check out this post to know how to clone a phone with Spyier.
Spyier – The Most Covert Software
Spyier is hands-down the best phone monitoring solution that we have tested. The tool is pretty efficient and gets the job done with complete secrecy. This application has been picked up extensively because of the way it comes handy in both professional and household usage.
Spyier has been present in the phone spy industry for well over a decade. The tool has been able to establish itself and acquire millions of users in more than 190 countries. This fact indicates its excellence in both reliability and security.

Corporate giants like The Verge, Mac World and PC World have not only reviewed Spyier, but have also given it the title of the best software for the year 2020! The tool draws sharp contrast with its rival spy solutions, in two aspects:
- It has been crafted using cutting-edge tech to offer optimum data security. None of the data from the target device is stored on its servers, thus preventing any sort of data theft.
- You don’t need to jailbreak or root the device that you wish to clone when using Spyier. This ensures that the target device’s warranty doesn’t become void, and also, it doesn’t become prone to malware.
- To work with Spyier, you don’t need to install anything on your own phone or computer. An online dashboard serves as the real-time mirror to all data from the target device. This dashboard can be accessed by logging in using ANY web-browser (desktop or mobile).
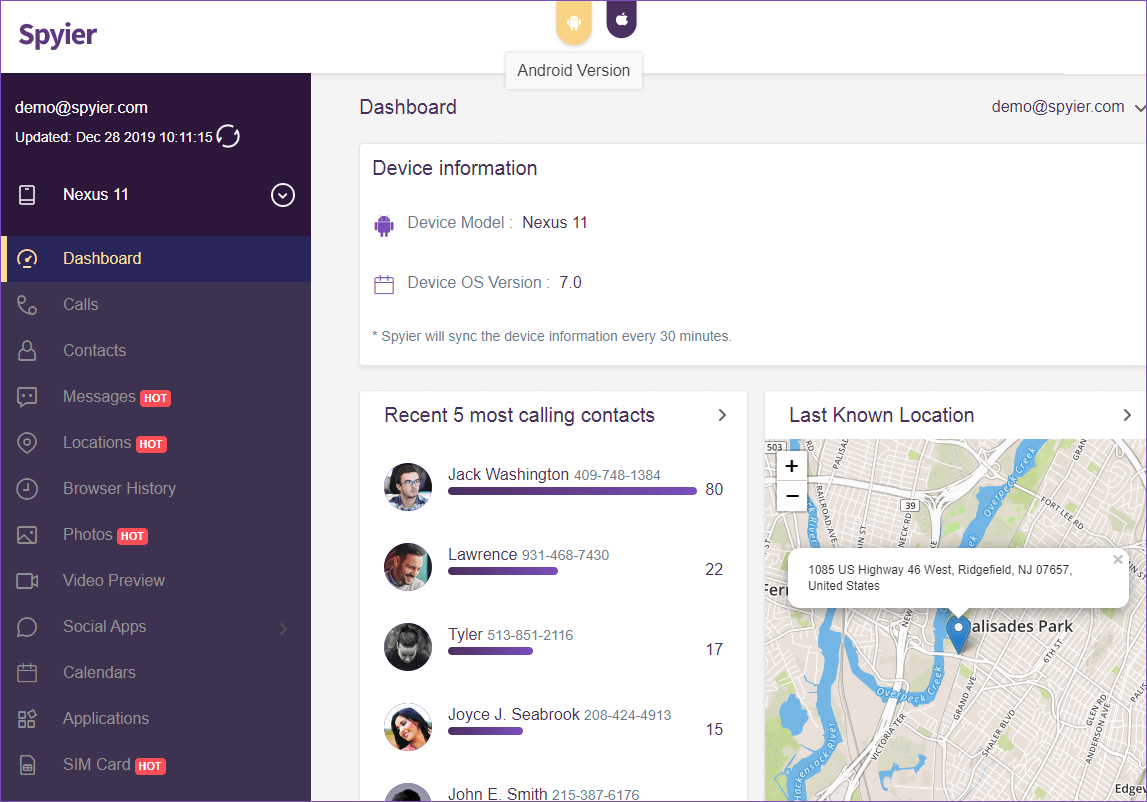
With such a keen eye for protecting user data privacy, no wonder Spyier is claimed to be the safest phone monitoring and cloning app currently available.
A Brief Look at the Features Unique to Spyier
Following is the list of features which enables Spyier to outperform its rivals:
- Spyier offers you the capability to hack into all social media applications and email accounts the target uses. It even lets you spy on the tiniest data exchanges like GIFs exchanged in a chat!
- The tool gets you complete access to the contact book and call logs from the target device. It even shows you the duration of incoming and outgoing calls and the time they were made or received.
- This software fetches you all the media files present on the target device. Not only does it collect those files which have been previously deleted, but it also gets those images which have been exchanged on social media.
- You can keep track of all SMSs exchanged using the target device using Spyier. It even lets you recover deleted messages!
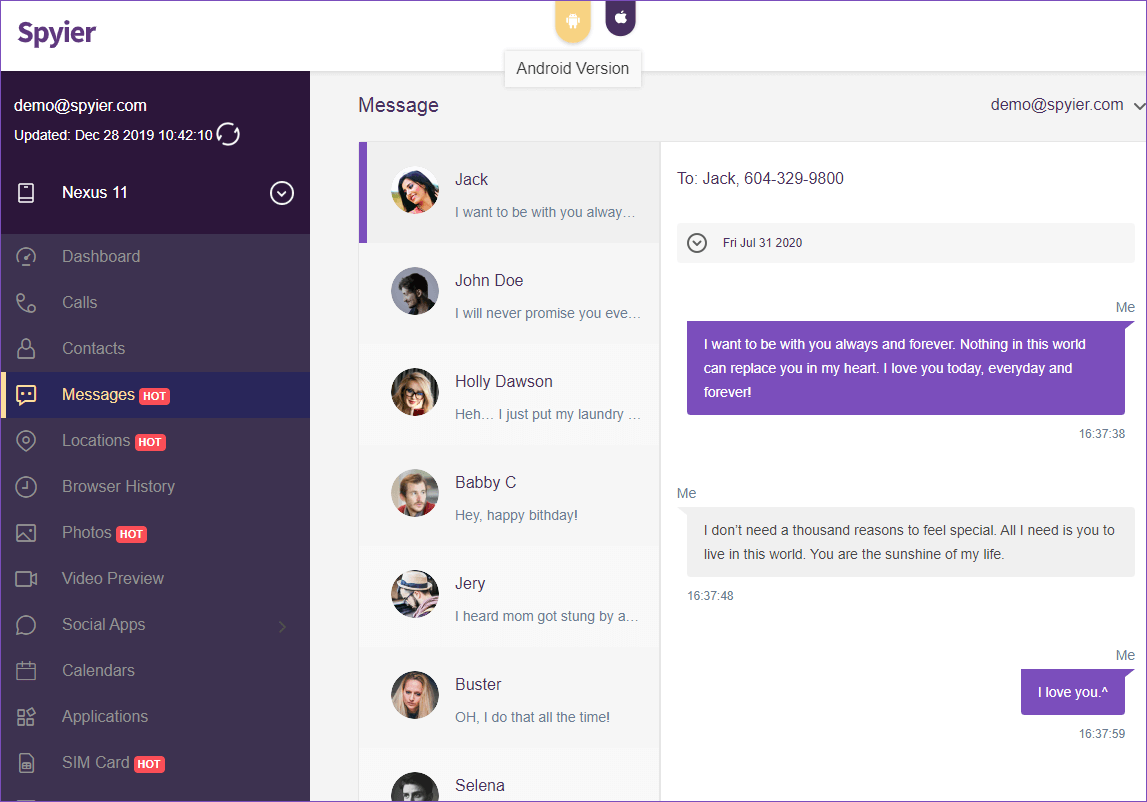
- The Android version of the tool comes equipped with a key-logger feature which helps record keystrokes on the target device. The recorded keys can then be rearranged to generate a possible password for any social media or email account.
- Spyier also gives you complete access to any internet searches that have been made by getting you the browser history.
- The tool is capable of not only tracking the GPS location of the target device 24/7, but also get a 3D street view of where the target is.
Spyier Works Well on both iOS and Android Platforms
Though the application works well on both Android and iOS platforms, its best work comes out with the latest versions of both OSs.
The Android version of Spyier needs installation on the target device. It is lightweight (merely 2MB), has lag-less performance, and does not affect the OS or the device. Due to this small size neither does it drain excess battery nor does it get detected by the user.
It runs quietly in the background without raising any red flags. Once installed, hiding the application is also very easy. All that one has to do is remove the icon from the application drawer and the tool is hidden!
For the iOS version, the functioning is even simpler. All you require are the target’s iCloud credentials to get inside the device. Once filled in, the tool starts syncing with the target’s iCloud backup.
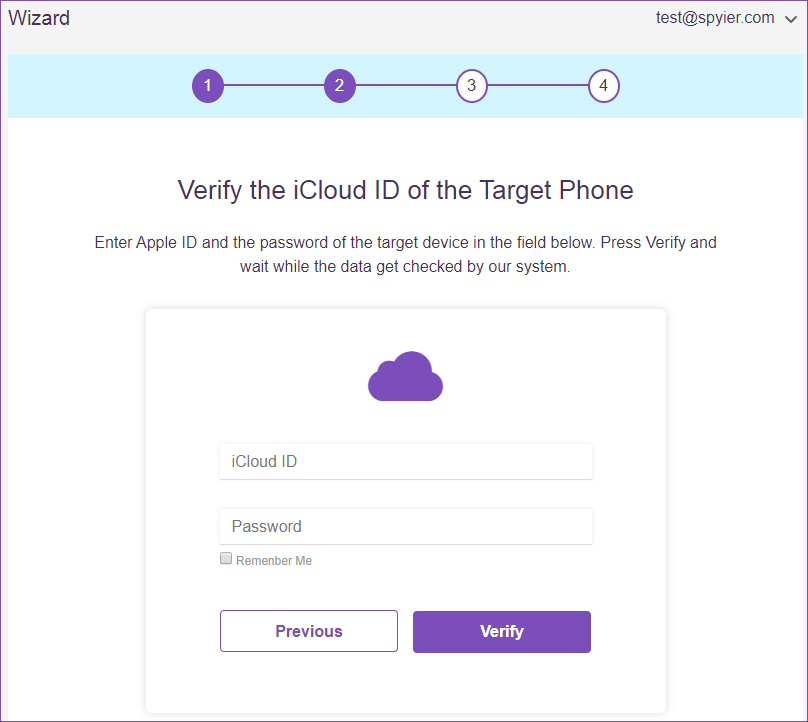
To clone and keep a tab on the device, remote access is provided. And since the application is completely web-based, to check the data on the target device all you need is a web browser to access your Spyier dashboard from.
To Conclude
In our opinion, Spyier is the best iPhone spy solution to clone a device. The tool is not only easy to pick up but is also very efficient in getting things done. This application is completely reliable and is capable of replicating the target device in less than 5 minutes!
The software is also pretty affordable and is tough to detect since it works in the background without giving itself away. Cloning a device never seemed simpler, did it?

![How to Clone a Cell Phone [Updated 2020]](https://cdn.mycplus.com/mycplus/wp-content/uploads/2020/11/spyier-banner.jpg)



