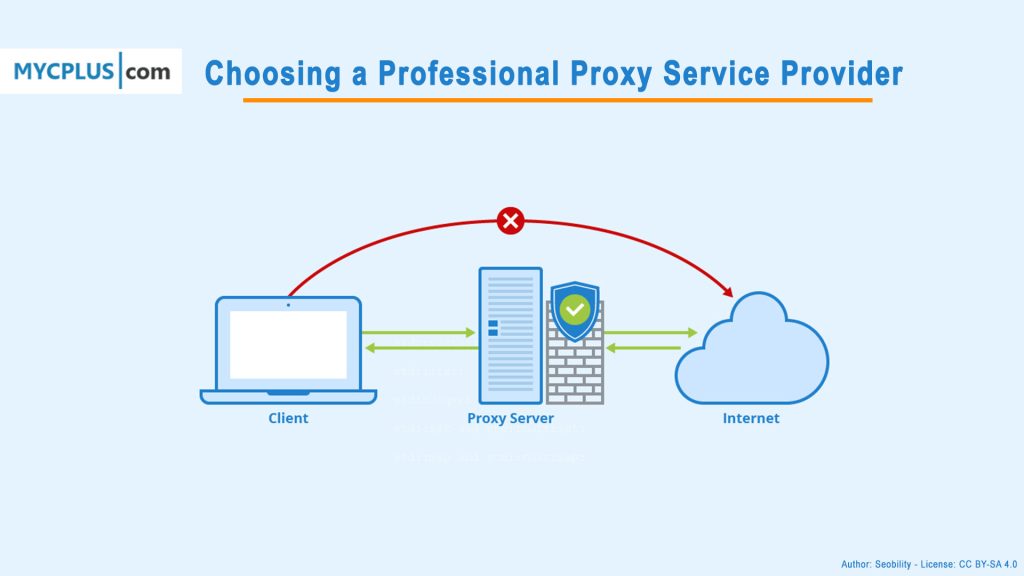
How Much Security Is Too Much?
It’s excellent to take the initiative regarding digital safety. But it’s best to resist the urge to install as many security programs as possible. Carefully consider the vulnerable parts of your devices and secure them, drawing as little attention as possible.